AI-Powered Recipe Generator: Cook Delicious Dishes with What You Have!

Cooking can be fun, but figuring out what to make with the ingredients in your kitchen can be tricky. That’s where our Recipe Generator comes in! This smart application uses AI to help you create delicious recipes based on the ingredients you already have. In this showcase, we’ll share how this application works and how […]
Securing AI Applications with LlamaGuard

LLM-based Input-Output Safeguard for Human-AI Interaction As artificial intelligence becomes increasingly integrated into everyday interactions, ensuring the safety and ethical use of AI systems is crucial for building trust, safeguarding users, and promoting responsible innovation. A key concern in AI deployment is preventing harmful, inappropriate, or unsafe content from being generated, particularly in applications where […]
Real-Time Data Streaming with AWS Kinesis
In today’s data-driven world, the ability to process and analyze information in real-time has become a game-changer. AWS Kinesis is a powerful service designed to enable developers to collect, process, and analyze real-time, streaming data efficiently. In this blog, we will explore the features of AWS Kinesis and walk you through a hands-on demo showcasing […]
Simplifying Data Workflows: A Deep Dive into ETL
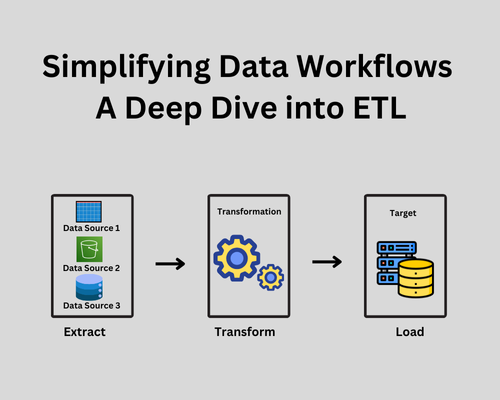
In today’s data-driven world, businesses generate large amounts of raw data daily. Transforming this raw data into meaningful insights requires effective data processing workflows, where ETL (Extract, Transform, Load) plays a crucial role. ETL simplifies the movement and transformation of data, empowering organizations to make informed decisions and gain a competitive edge. This blog dives […]
Mastering Data Transformation with AWS Glue and Query using Athena
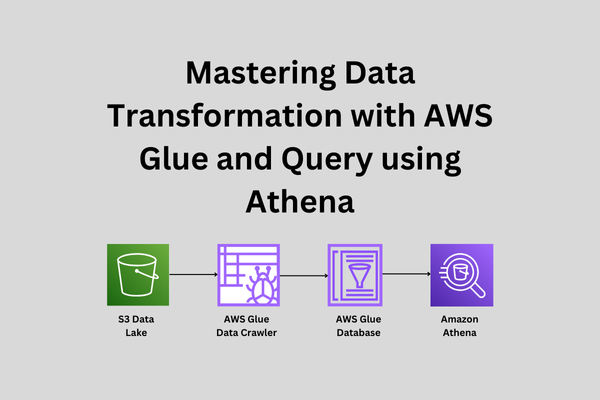
In the era of large-scale data, organizations are collecting vast amounts of information from various sources. However, raw data is often unstructured and messy, making it challenging to extract valuable insights. Data transformation tools are essential for cleaning, organizing, and preparing data for analysis. Amazon Web Services (AWS) offers two powerful tools, AWS Glue and […]
Cloud Computing for Large-Scale Data Analytics On AWS

In today’s data-driven world, organizations collect massive amounts of data daily. Analyzing this data is crucial for gaining actionable insights, predicting trends, and making data-informed decisions. While traditional on-premise setups have been instrumental in large-scale data analytics, they present significant challenges as data volume and complexity grow. The shift to cloud computing has revolutionized data […]
Dynamic Secret Management in Azure

In cloud-native applications, securely managing and updating secrets like API keys, passwords, and connection strings is vital. Manually updating secrets in your application every time they change can be challenging and error-prone. This is where dynamic secret management comes into play, allowing real-time secret updates from a central, secure store. This blog covers implementing dynamic […]
Streamlining Application Monitoring and Insights with Azure Application Insights

In today’s cloud-centric world, effective monitoring is key to maintaining the health of any application. Azure Application Insights (App Insights) is a powerful tool that helps developers gain real-time insights into their applications’ performance and usage patterns. Whether you’re running applications in the cloud, on-premise, or in a hybrid environment, App Insights offers actionable insights […]
Understanding Ingress in AKS

Kubernetes is a powerful tool for managing containerized applications at scale, and Ingress plays a crucial role in controlling external access to your services. In this blog, we’ll dive deep into Ingress in Azure Kubernetes Service (AKS), why it’s essential, and how to configure it, including setting up NGINX Ingress Controllers, using Azure’s Application Routing […]
How to manage secrets in Azure?

In today’s cloud-driven world, managing sensitive information such as API keys, passwords, and connection strings securely is crucial to ensure the security and reliability of your applications. Azure Key Vault offers a robust, centralized solution for managing secrets, encryption keys, and certificates. In this guide, we will explore how to manage secrets in Azure using […]

